Twitter’s SMS 2FA move is good for everyone, and here’s why.
EBONY S. MUHAMMAD
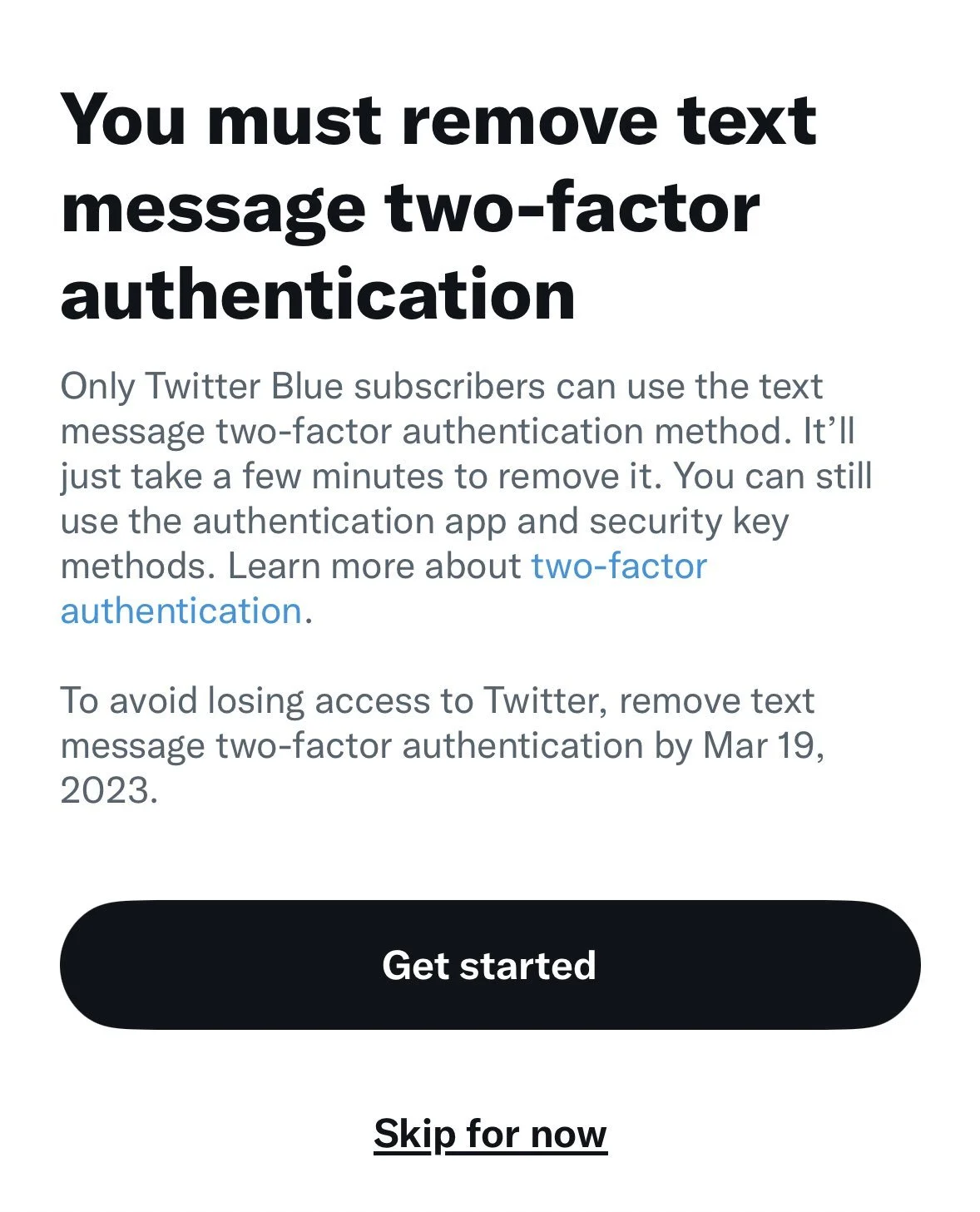
If you use Twitter, I’m sure you’ve received the pop-up notification on February 17, 2023, upon logging in, that SMS two-factor authentication (2FA) will no longer be available unless you’re a Twitter Blue Subscriber. This could seem like an immediate security breach enabling potential hacking on the surface, but in reality it’s a good move for everyone.
According to the recent blog post by Twitter dated February 15, 2023:
“While historically a popular form of 2FA, unfortunately we have seen phone-number based 2FA be used - and abused - by bad actors. So starting today, we will no longer allow accounts to enroll in the text message/SMS method of 2FA unless they are Twitter Blue subscribers. The availability of text message 2FA for Twitter Blue may vary by country and carrier.”
According to Tearline, Elon Musk disclosed (on Spaces) that the company was losing over $60M annually for the SMS 2FA feature.
“…Twitter was being scammed to the tune of 60 million dollars a year for SMS texts, not counting North America… Basically, there are telcos who are not being super honest out there, in other parts of the world, who were basically gaming the system and running, like, two-factor authentication SMS texts over and over again, and just creating a zillion bot accounts to literally run up the tab so that Twitter would SMS text them, and Twitter would pay them millions of dollars, without even asking about it.”
You may be thinking that this is a great business move for Twitter, but what about the Twitter users. One of the most important reasons this is a good move for Twitter users, who are not Twitter Blue Subscribers, is that SMS 2FA is the weakest in terms of security. Why? It has been exploited extensively in the past by rerouting text messages.
What is the alternative? There are two: Authenticator Apps and Security Keys.
According to PCmag.com:
“It turns out that clever crooks can reroute text messages. But, as lead software analyst at PCMag Michael Muchmore writes, if you use an authenticator app instead, the codes generated on your phone never travel through your mobile network, cutting down the risk for exposure.”
In my own research, I’ve seen many in the Cybersecurity network agree that SMS 2FA is in fact weaker and more prone to security breaches, and because they are more “convenient” for the everyday user, it makes it increasingly available to exploit.
Fortunately, the user can simply go to their app store and download the Authenticator App of their choice, based on the type of phone (IOS or Android) they use. I won’t recommend any in particular for the above reasons, but I highly encourage you to visit your app store and use the Authenticator App that is highly rated/reviewed and recommended for your phone. Don’t over complicate it.
To wrap this up: Twitter’s move to eliminate SMS 2FA for non-Twitter Blue Subscribers is actually a good thing for both the business and the end user. I can appreciate the security measures, especially after doing my own research. That’s what we must do, our own research.
If you’d like a deeper understanding of multi-factor authentication, I released an easy to digest email last year during Cybersecurity Awareness Month.
Stay safe and feel free to share this!
JOIN US AND TAKE BOLD STEPS TOWARDS DIGITAL DEFENSE + TECHNOLOGY